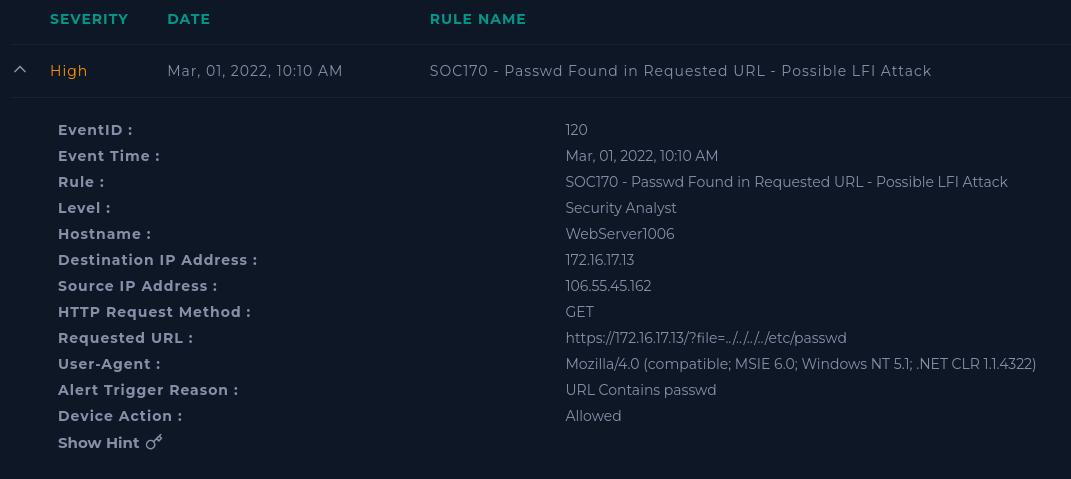
Let's start with our alert:
Click Create Case and let's get started.
The evidence is right there in the alert, but let's go check the logs anyway. Go to Log Manaement and search for the source IP (106.55.45.162).
There is only one event:
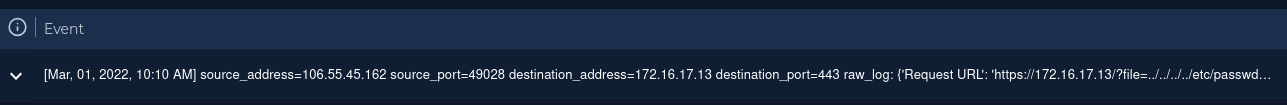
Expanding the event, shows the log entry:
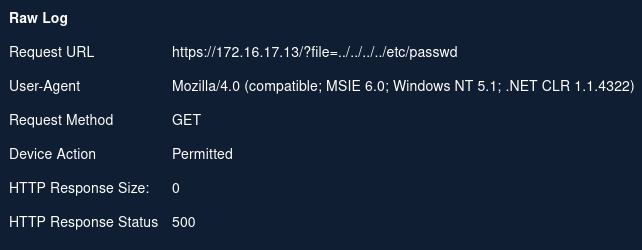
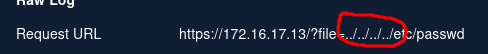
The URL shows an attempt to use directory traversal to display etc/passwd
Okay, we should have enough information to do the playbook.
Is traffic malicious?
Yes. There is no realistic way that a user would accidentally add that payload to the file parameter.
What is the attack type?
LFI & RFI. Directory traversal back down to a root directory like etc is a classic example of a Local File Inclusion attack.
Check if it is a planned test
Not planned. There was no email from April 1 to March 7, 2022 indicating a test.
What is the direction of traffic?
Internet to Company Network. The source IP (106.x.x.x) was from outside and the destination IP (172.x.x.x) was inside.
Check whether the attack was successful
No. The HTTP Response Size: 0 and HTTP Response Status 500 both indicate that the server did not process the requested URL.
Add any artifacts, such as the attacker IP address.
Do you need Tier 2 escalation?
No. The attack was not successful, so no need to escalate.
Add any analyst comments.
Close the alert.