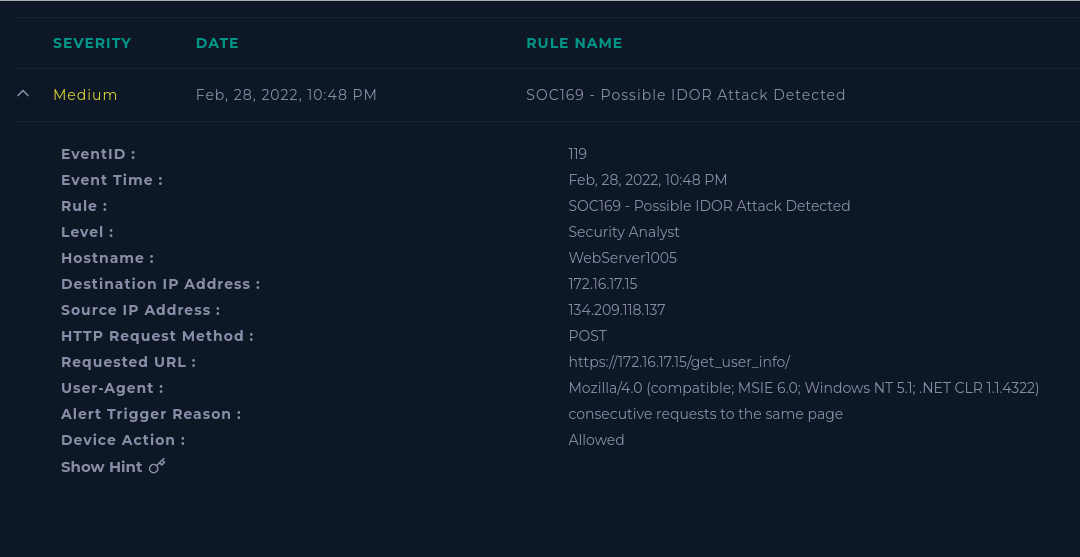
Here is our alert:
Click on Create Case and let's take a look.
First, let's go to Log Management and see if there are more details.
For simplicity, I changed to the basic mode. Searching for our source IP address (134.209.118.137) gives us five entries.
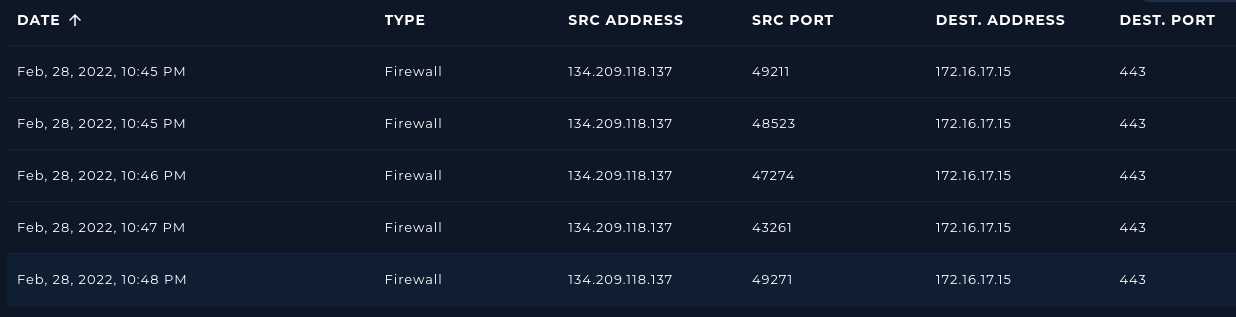
Each of the logs shows the same situation:
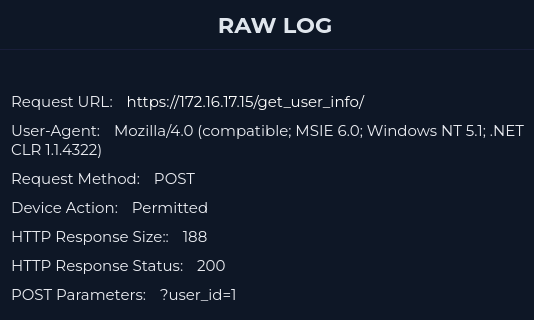
However, pay attention to the user id parameter.
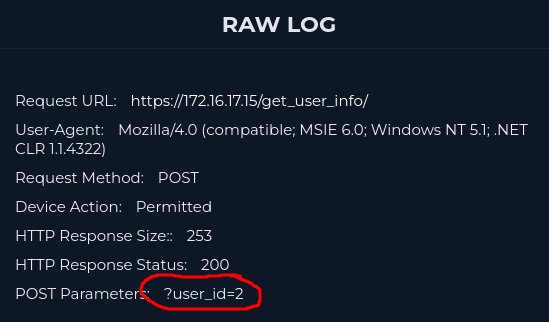
Our bad guy tried user_id 1 to 5 in sequence.
We should have enough information to run the playbook.
Is the Traffic Malicious?
Yes. The attacker was clearly trying to access other users' information by changing the user_id parameter.
What is the Attack Type?
IDOR. The sequential parameters is a tell-tale sign of an attempted Insecure Direct Object Reference.
Check If It Is a Planned Test
I found no emails during the month of February 2022 indicating a test.
What is the direction of the traffic?
Internet to Company Network. Our source address was outside (134.x.x.x) while our destination was inside (172.x.x.x).
Check whether the attack was successful.
Successful. Each log entry showed HTTP Response Status: 200 and the sizes of the responses were different, indicating different user information presented on each page.
Contain WebServer1005 as instructed.
Add artifacts like the attacker IP address.
Do you need Tier 2 escalation?
Yes, because the attack was successful.
Summarize what was done in the notes and close the alert.