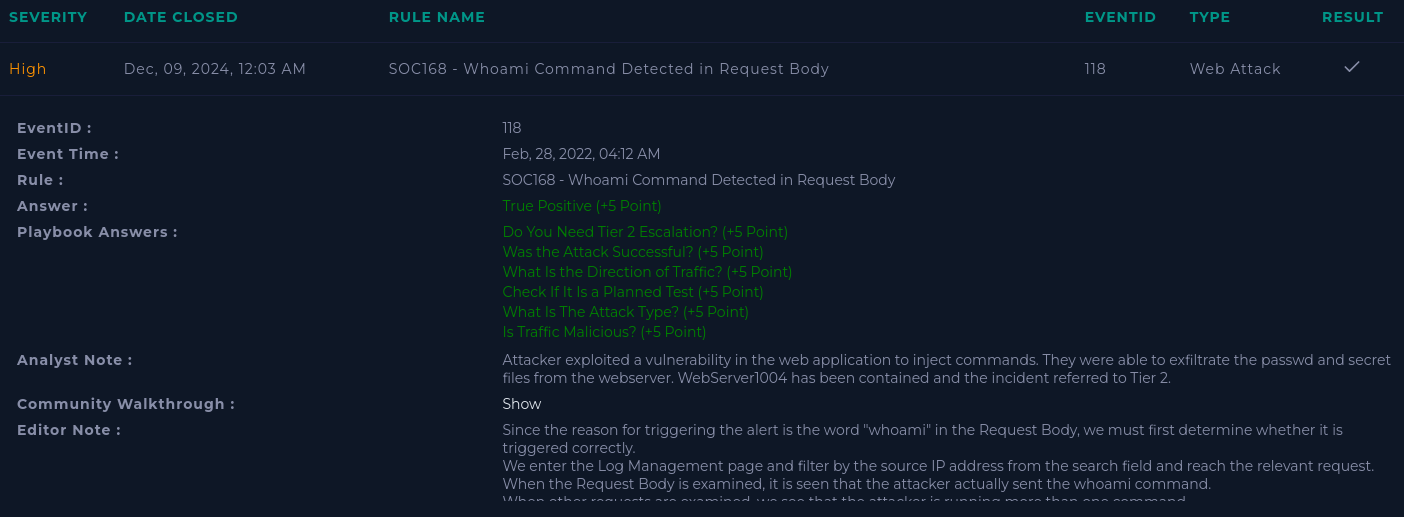
Here is our alert:
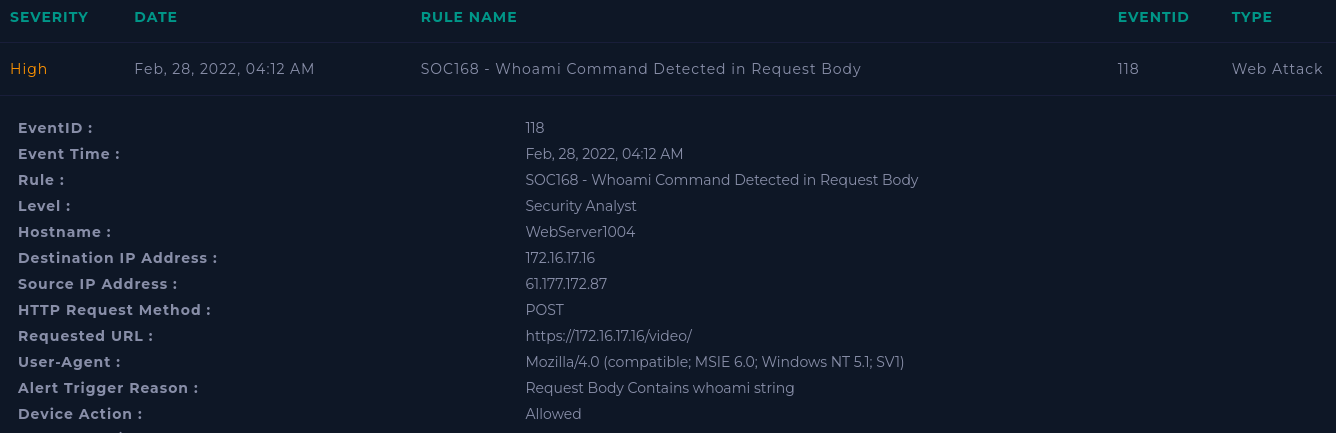
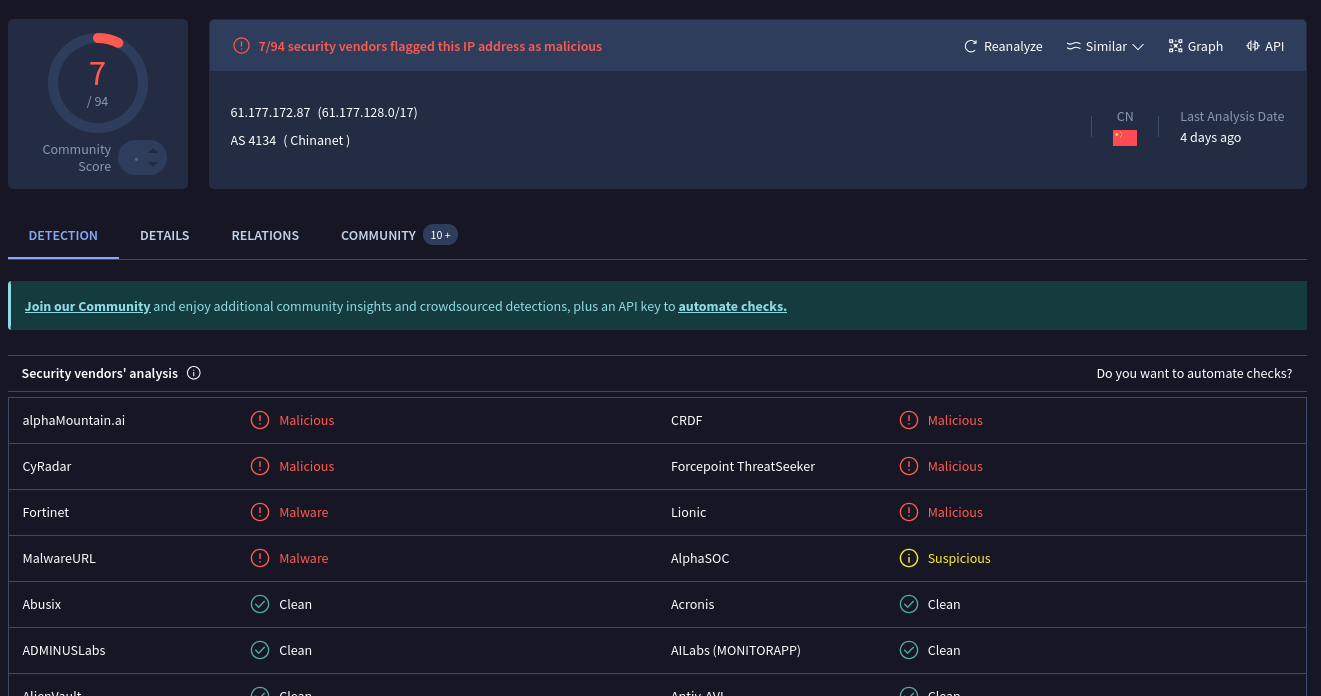
Let's check the IP in Virus Total:
Definitely Chinese and some vendors are flagging it.
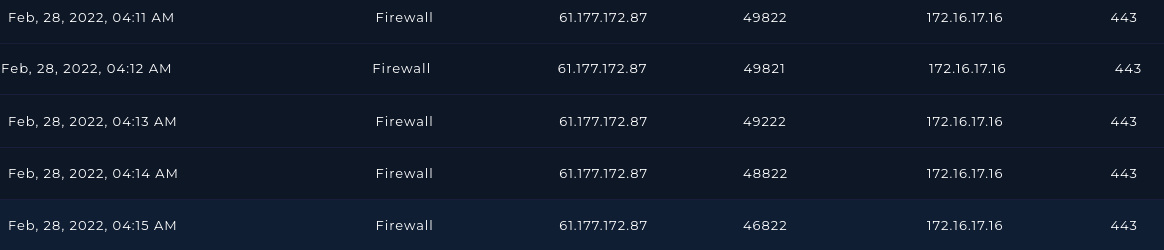
Next, let's look at the log:
The alert triggered on the second request, but there were five. The attacker was apparently trying to exploit a command injection vulnerability.
The commands in the c= parameter were ls, whoami, uname, cat etc/passwd, and cat etc/shadow.
These were successfully passed to the the webserver:
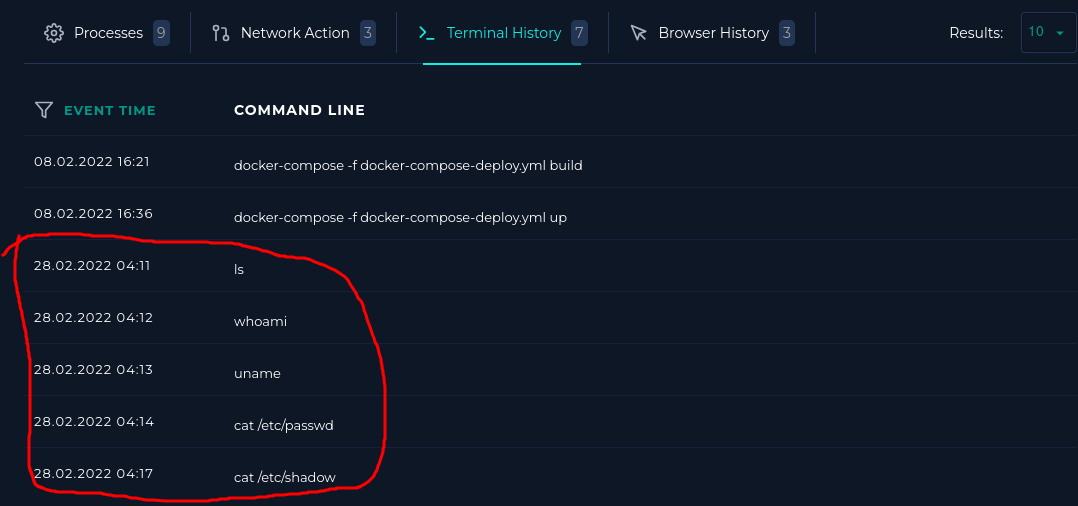
I have contained the webserver and Tier 2 should be notified.
We should have enough to do the Playbook.
Is traffic malicious?
Yes.
What is the attack type?
Command Injection
Check if it is a planned test?
No email or other evidence of a planned test.
What is the direction of the traffic?
Internet to Company Network. The source IP was outside of the network.
Check wither the attack was successful.
Since the commands were echoed in the command line of the webserver, and showed corresponding processes, the attack was successful.
Containment
Contained.