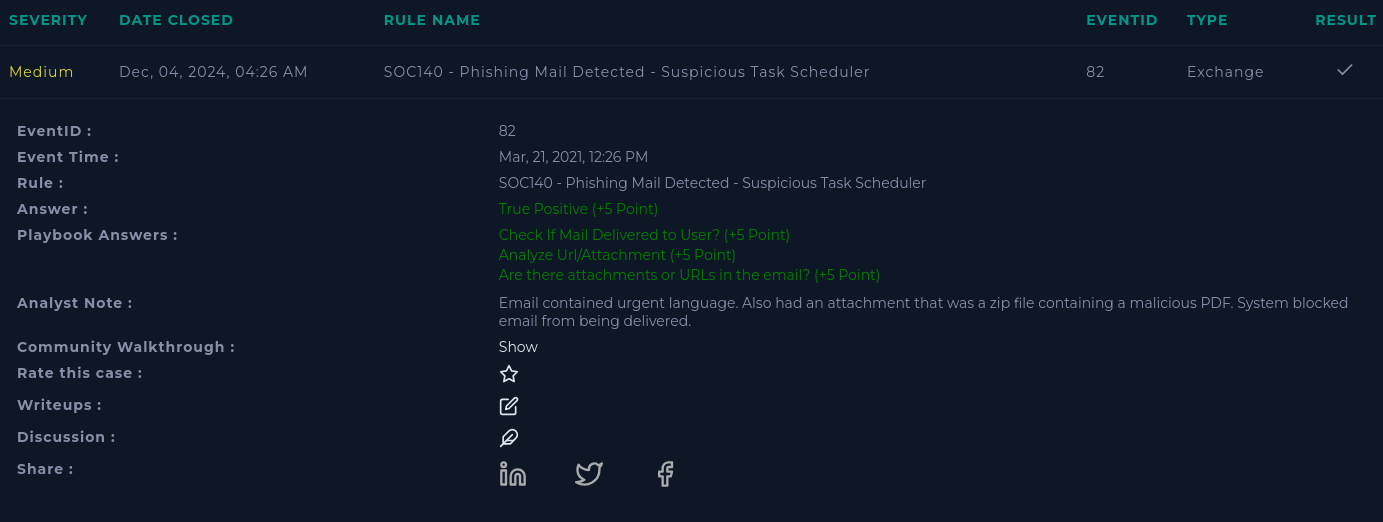
Here is our alert:
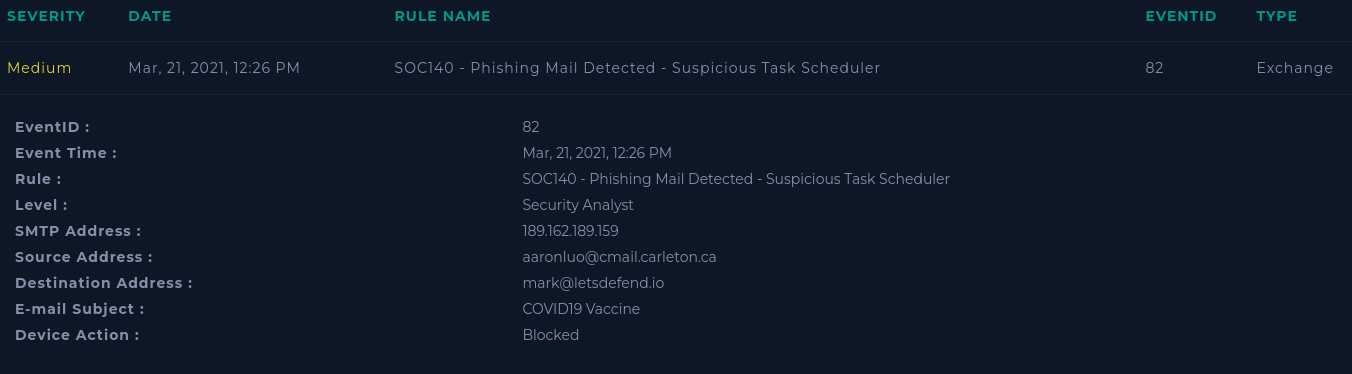
First let's look at the actual email:
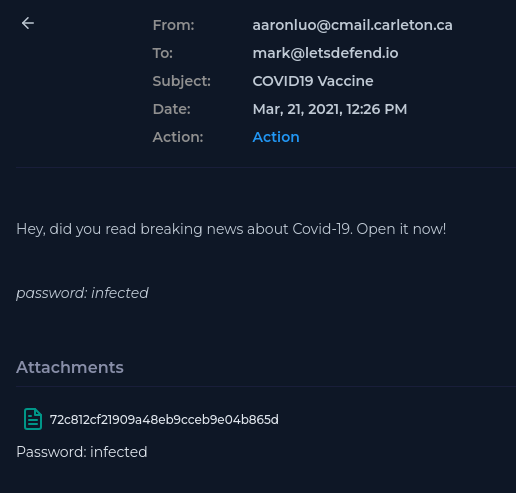
That certainly looks suspicious. "Open it now!" creates a sense of urgency. Also, that is a very strange name for a file.
Extracting the zip file reveals Material.pdf
If we take the sha256 hash (39fb927c32221134a423760c5d1f58bca4cbbcc87c891c79e390a22b63608eb4) to Virus Total, the nature of the file is pretty obvious.
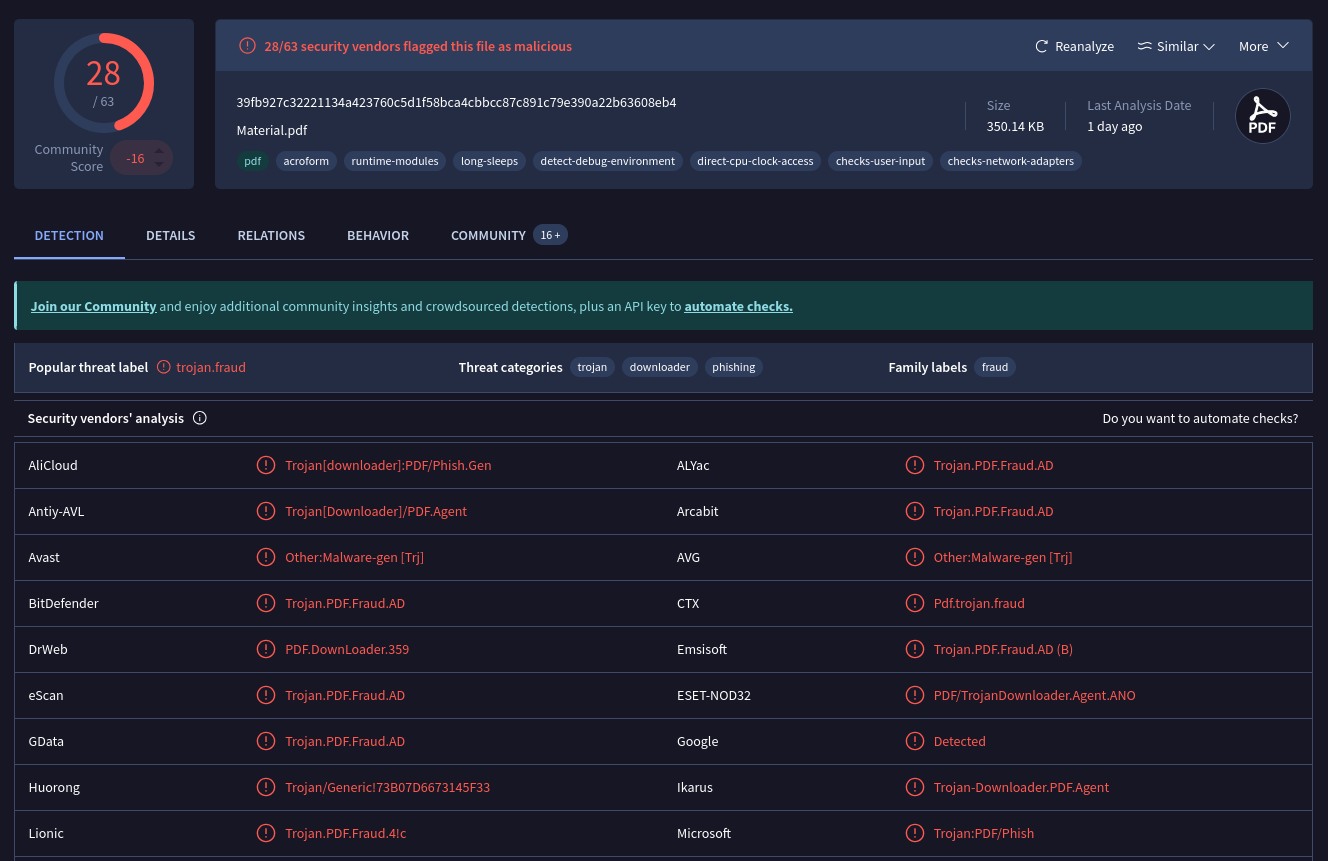
We probably have enough to do the playbook.
Are there attachments or URLs in the email?
Yes. There is an oddly named zip file.
Analyze URL/Attachment
Malicious. Lots of evidence on Virus Total.
Check if mail delivered to user?
Not delivered. The alert shows Device Action: Blocked